Since Pandemic, Autopilot has taken main stage at various organizations as it enables organizations to procure devices from vendors and ship it directly to end user’s home. While the Device Configurations and Application Management can be done through Intune, lot many times, organizations want to deploy specific set of policies and applications to specific set of devices. This could be based on geography, project, department etc., This can be achieved by grouping the devices in Azure Active Directory and using targeting the policies and applications accordingly.
The challenge however is on grouping the device objects dynamically. This can be solved by specifying Group Tag for each device while uploading the device hardware hashes.
This aspect is detailed in this post and several other posts linked in the same blog.
You can ask your vendor to update the Group tag Information if they are uploading the hardware hashes to autopilot service. This may work 1) if your vendor agrees to do and 2) you have simple tagging requirement like country or location based.
For devices that you import the hardware hash by booting up the device, you can refer to this blog and the powershell script supports -GroupTag parameter where you can mention appropriate group tag for the device.
If your organization has bought several hundred autopilot devices, the hardware hashes are already uploaded and if the IT team wants to group them according to location, projects, geography, this is a manual task to identify each device under Autopilot Devices and update the Group Tag accordingly.
This blog post helps in automating the above-mentioned process through Graph API.
To automate the process, you need a PowerShell script which has capability to read devices list from CSV (based on device serial), authenticate with Azure AD and talks (post data) to Graph API endpoints for each device that you need to update the Group Tag.
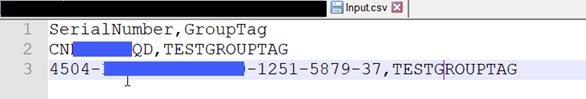
Prepare CSV File:
Create a CSV File with SerialNumber and GroupTag mapping as per your organization needs. This can be project based, location based, country/geography based or combination like “Asia-India-GKLab”. Save it in local computer where you intend to run the script.
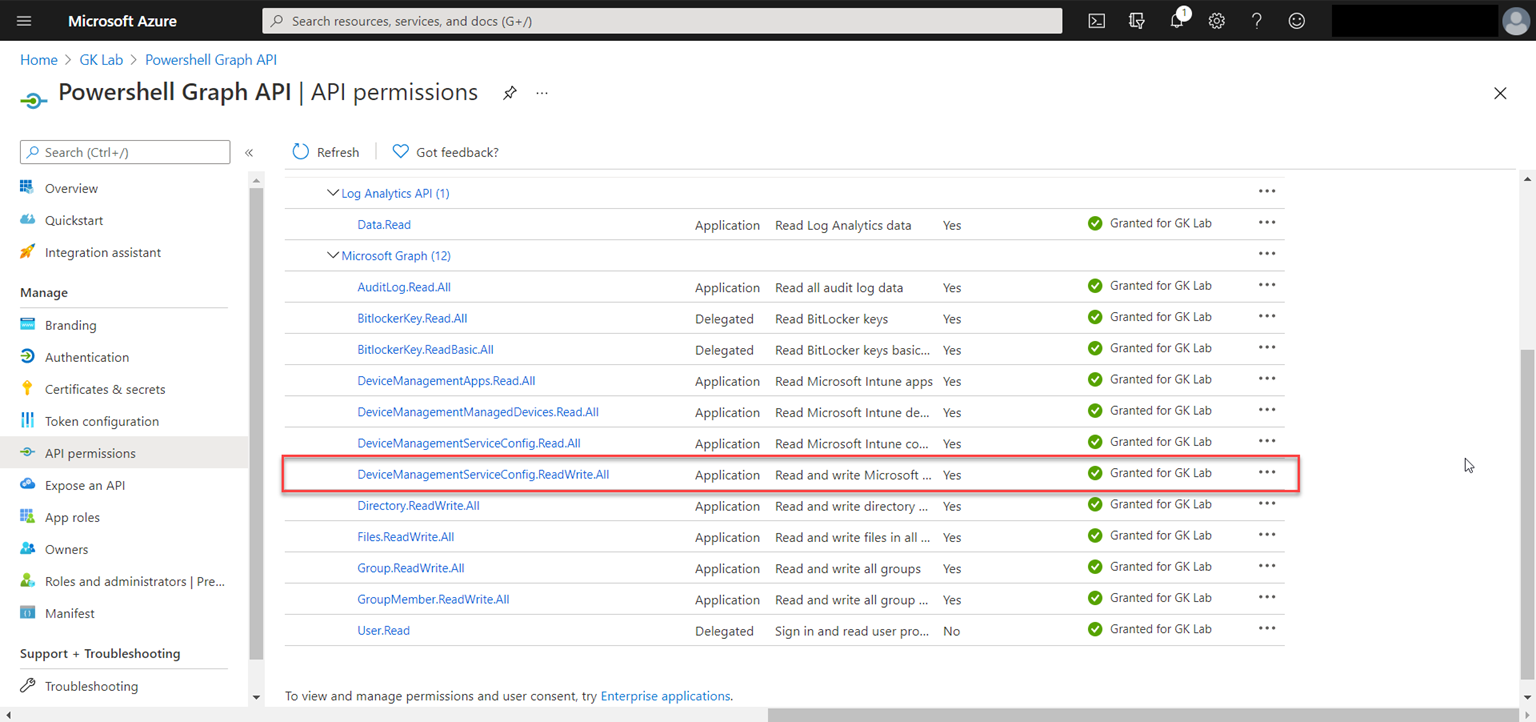
Register Azure AD Application for Authentication:
To authenticate with Graph API, we must register an Azure AD Application or use existing application with below permission and grant consent as Global Administrator. The permission can be Application or Delegation type.
Application type does not need the user who runs the script to be authenticated. Hence this type of permission can be used for unattended execution of scripts (through task scheduler or by other applications.
Delegation type requires the user who executes the script to be authenticated against Azure AD and have necessary permission that the script is intended to do.
Detailed documentation on how to register an Azure AD Application can be found in this post.
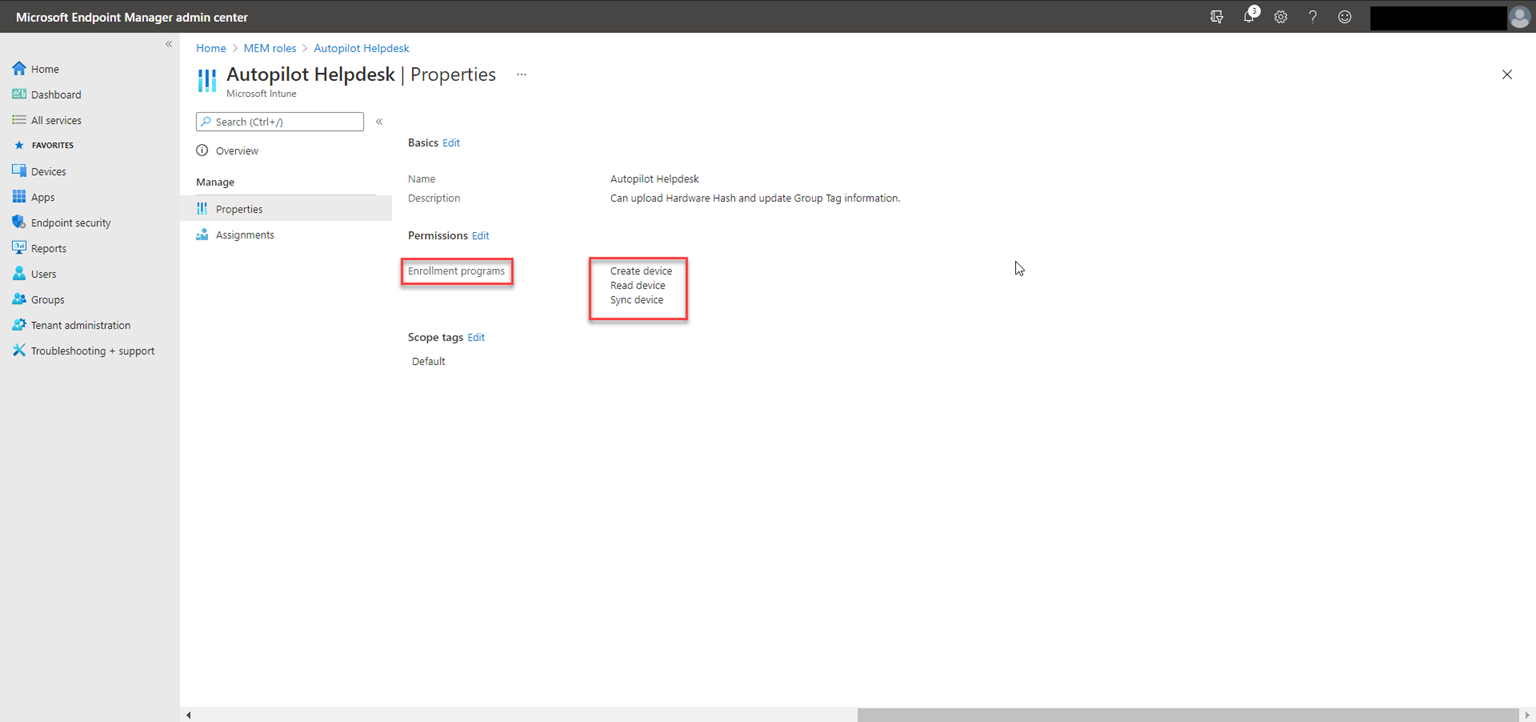
Once the Application is registered, capture the Tenant Id, Client Id and Client secret.
If you have chosen delegate permission, create a custom RBAC in Intune and add the users who will be executing the script to this role.
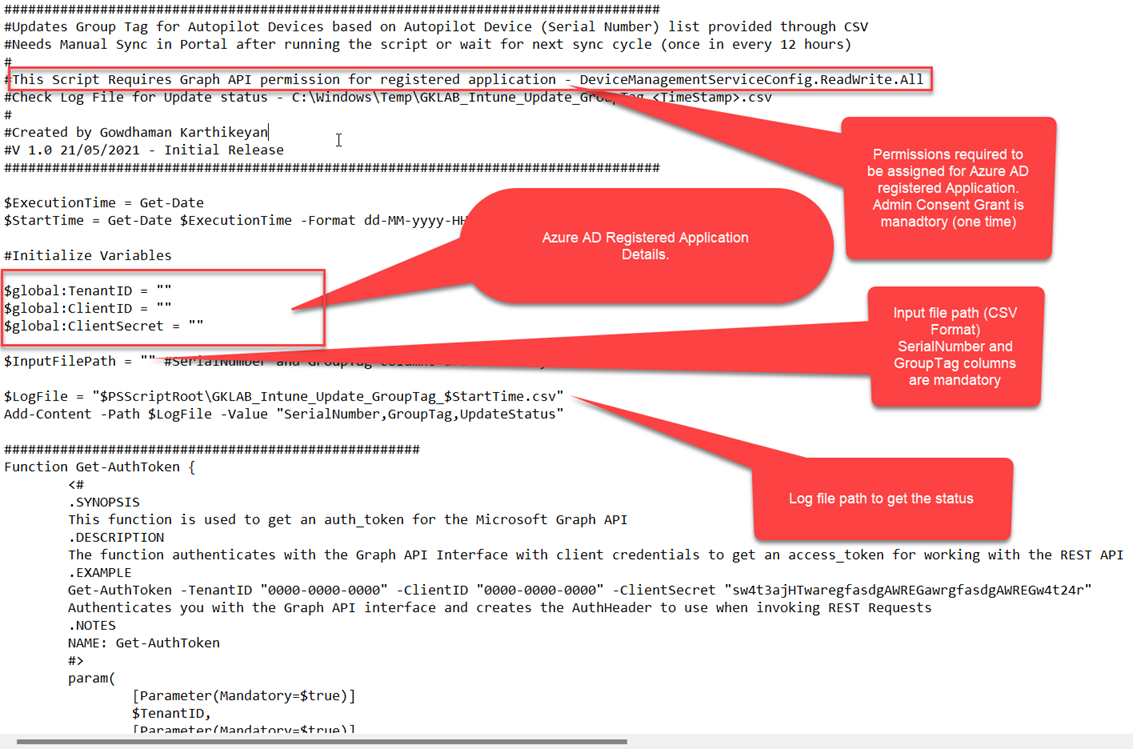
Download and Setup Script:
Download the script from here and configure as per below guidelines. Save the script.
Execution and Validating Results:
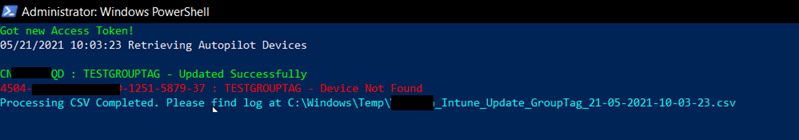
Once the script is configured with appropriate values, launch PowerShell as administrator and execute the script.
You will notice the results on screen as well as logged in a logfile for future reference.
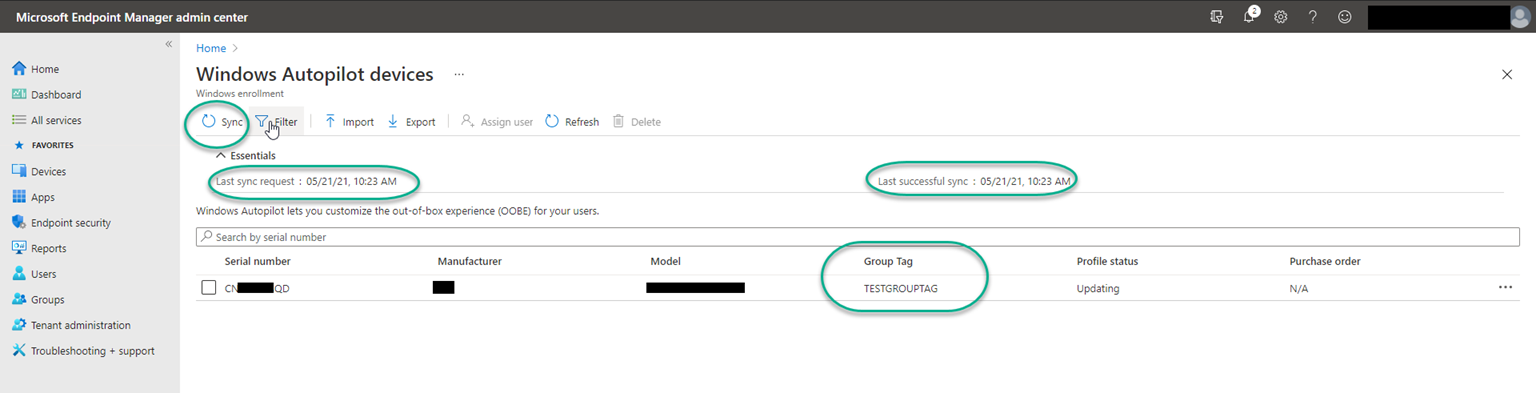
You can validate the same in Endpoint Portal as well. Remember, the sync happens every 12 hours or you can initiate a manual sync.
Hope you enjoyed automating group tagging of your devices!
