Intune provides ability configure BitLocker Drive Encryption on devices that run Windows 10/11. Some settings for BitLocker requires the device to have a supported TPM.
Current encryption reports in Intune:
Intune provides a built-in encryption report that presents details about the encryption status of devices across all your managed devices. After Intune encrypts a Windows device with BitLocker, you can view and manage BitLocker recovery keys when you view the encryption report. In the report, the “Encryption status” column provides the device’s encryption status.
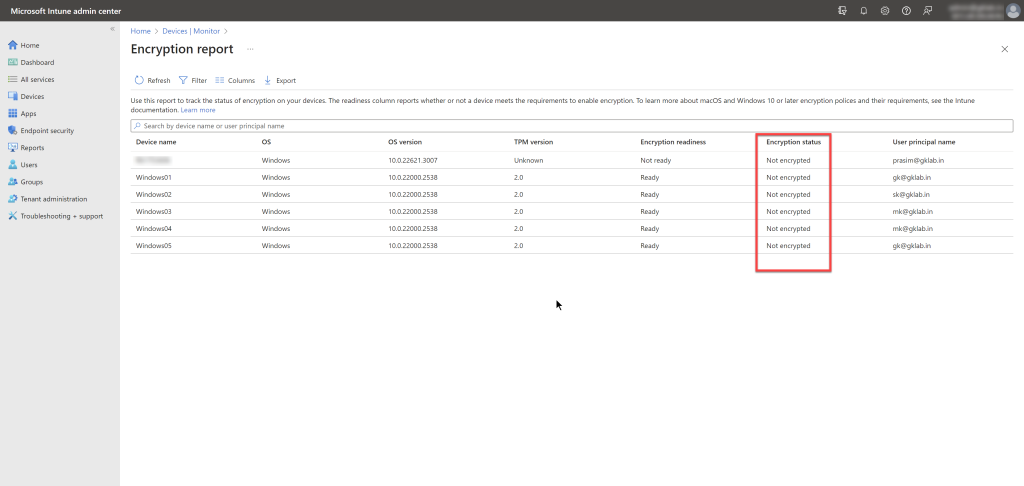
As you click each device in the report, a details pane opens up and has a “Status details”. This provides additional details based on the information from Bitlocker CSP which includes whether the device has a encryption policy, reason for encryption failure including the recovery key backup state etc., While this is not available as additional column in UX, this information is included when you export the data.

Problem Statement:
As customers look to migrate Bitlocker management from MBAM/ConfigMgr, they are looking for a report that provides visibility into devices that don’t have their recovery keys backed up in Entra ID. This is required for the admins to be proactive and avoid situations where a device enters recovery without the recovery key backed-up in Entra ID leading to data loss for end users.
Workaround using PowerShell Scripts and Graph API:
Here is a sample script which can be used to obtain list of Intune devices which doesn’t have the OS drive’s recovery key backed up to corresponding Entra ID device objects.
The script requires Microsoft Graph PowerShell modules. You can install these using the commands below. Refer to Install the Microsoft Graph PowerShell SDK documentation for more info.
Install-Module Microsoft.Graph
Install-Module Microsoft.Graph.BetaThe user account under which the script is executed should have minimum set of below permissions. The script requires an Entra ID sign in and a consent will be requested to proceed further.
BitLockerKey.ReadBasic.All
DeviceManagementManagedDevices.Read.AllThe script accepts an $OutputFolder as parameter and on succesfull excution, will create a CSV file in the path, with list of Intune devices that do not have OS recovery key backed up in Entra ID. The output will contain below properties.
- AzureAdDeviceId
- ComplianceState
- DeviceName
- EmailAddress
- EnrolledDateTime
- IsEncrypted
- Id
- LastSyncDateTime
- OSVersion
- OperatingSystem
- SerialNumber
- UserDisplayName
- UserPrincipalName

<#
DISCLAIMER STARTS
THIS SAMPLE CODE IS PROVIDED FOR THE PURPOSE OF ILLUSTRATION ONLY AND IS NOT INTENDED TO BE USED IN A
PRODUCTION ENVIRONMENT. THIS SAMPLE CODE AND ANY RELATED INFORMATION ARE PROVIDED IS "AS IS" WITHOUT WARRANTY
OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE IMPLIED WARRANTIES OF
MERCHANTABILITY AND/OR FITNESS FOR A PARTICULAR PURPOSE."
DISCLAIMER ENDS
#>
param(
$OutputFolder = "C:\Windows\Temp"
)
$Now = Get-Date -Format "dd-MM-yyyy-HH-mm-ss"
$ReportFile = "$OutputFolder\Devices_Without_OSDrive_RecoveryKey-$($Now).csv"
$Stopwatch = [System.Diagnostics.Stopwatch]::StartNew()
#Connect to Microsoft Graph using delegated permissions
Write-Output "Connecting Microsoft Graph..."
Connect-MgGraph -Scopes BitLockerKey.ReadBasic.All,DeviceManagementManagedDevices.Read.All
Write-Output "Retrieving all Intune managed Windows devices..."
$IntuneWindowsDevices = Get-MgDeviceManagementManagedDevice -Filter "operatingSystem eq 'Windows'" -All `
-Property AzureAdDeviceId,ComplianceState,DeviceName,EmailAddress,EnrolledDateTime,IsEncrypted,Id,LastSyncDateTime,OSVersion,OperatingSystem,SerialNumber,UserDisplayName,UserPrincipalName
Write-Output "Retrieving all OS drive recovery keys from Entra ID..."
$AllOSDrivekeys = (Get-MgInformationProtectionBitlockerRecoveryKey -All) | where {$_.volumeType -eq 1}
Write-Output "Finding out Intune devices that do not have OS drive recovery key in Entra ID..."
$DevicesWithoutOSDriveKey_Intune = $IntuneWindowsDevices | Where-Object { $AllOSDrivekeys.DeviceId -notcontains $_.AzureAdDeviceId}
If ($DevicesWithoutOSDriveKey_Intune){
Write-Output "Generating output at $ReportFile ..."
$DevicesWithoutOSDriveKey_Intune | select `
-Property AzureAdDeviceId,ComplianceState,DeviceName,EmailAddress,EnrolledDateTime,IsEncrypted,Id,LastSyncDateTime,OSVersion,OperatingSystem,SerialNumber,UserDisplayName,UserPrincipalName | `
Export-CSV -NoTypeInformation -Path $ReportFile
} Else {
Write-Output "All Intune managed Windows devices have their OS drive recovery key backed up in Entra ID."
}
$Stopwatch.Stop()
Write-Output "Time Taken for the script execution:`n"
$Stopwatch.ElapsedNext Steps:
With the list of devices,
- Create a static security group of devices that are encrypted but not have their OS recovery key backed up in Entra ID and target a proactive remediation to back up the recovery keys.
- Create a static security group of devices that are not encrypted and target a Intune Bitlocker configuration policy.
- Add further automation to update one of the device’s extension attribute with bitlocker recovery key escrow status or encryption status and create dynamic device groups to accomplish above two outcomes.
Part 2 will cover additional scenarios on bitlocker encryption in Intune.
